Cyber-Security:

VPN (Virtual Private Network)
| Virtual |
- because it's as if you have a private connection directly to any website or another computer you connect to. |
| Private |
- because all your website visits and online activity is between you and the websites you visit. |
| Network |
- because you're using a special network of VPN servers that covers the entire globe. |
 What is a Virtual Private Network?
What is a Virtual Private Network?
A VPN is a means of creating a private network across an untrusted network such as the internet.
VPNs can be used for a number of different purposes such as:
 to securely connect isolated local area networks (LANs) across the internet
to securely connect isolated local area networks (LANs) across the internet
 to allow mobile users remote access to a corporate network using the internet
to allow mobile users remote access to a corporate network using the internet
 to control access within an intranet environment.
to control access within an intranet environment.
A VPN is:
 an easy way for corporate or private individuals to add an extra layer of security to their online activities.
an easy way for corporate or private individuals to add an extra layer of security to their online activities.
 a service that takes an internet connection and makes it more secure by masking the user's individual IP address with a temporary one, hiding their true IP address from every connection made online.
a service that takes an internet connection and makes it more secure by masking the user's individual IP address with a temporary one, hiding their true IP address from every connection made online.

 a service that your employer provides, or you sign up for online either as part of a anti-virus package or for a small monthly charge.
a service that your employer provides, or you sign up for online either as part of a anti-virus package or for a small monthly charge.
Once you have an account, your VPN service should be "on" when you're online.
You can consider it to be a 'cloak of invisibility' - allowing you to move freely around the web without detection.
VPNs encrypt your connections and make you virtually anonymous online. It reroutes your internet traffic through a server, making your activities appear to originate from that server instead of your personal IP address, allowing you to access to the web without being tracked, monitored, and identified.. So, ssing a VPN can make using the internet safer, more secure, and more private.
Think of it like this: If your car pulls out of your driveway, someone can follow you and see where you're going, how long you're at your destination, and when you return. They might even peek into your car to learn more about you, the driver. With a VPN, it's like driving from your house into an underground tunnel, exiting it into a closed parking garage, switching to a different car, and driving out. No one who was following you can know where you went.
 VPN within a corporate network
VPN within a corporate network
VPNs are typically implemented using dedicated network devices (sometimes this might be a firewall) and software.
There are two parts to the software:
 VPN client - this is installed on the computer of anyone who wants to be part of the VPN. The client is responsible for connecting users to the VPN so that it can send and receive information in a secure manner with, in this example, a corporate network.
VPN client - this is installed on the computer of anyone who wants to be part of the VPN. The client is responsible for connecting users to the VPN so that it can send and receive information in a secure manner with, in this example, a corporate network.
 VPN server - this is part of a dedicated network device, usually located on the perimeter of an organisation’s network. The server software typically performs the authentication of users and route traffic to the corporate network.
VPN server - this is part of a dedicated network device, usually located on the perimeter of an organisation’s network. The server software typically performs the authentication of users and route traffic to the corporate network.
The VPN software creates a path known as a ‘tunnel’ between the VPN client and the VPN server.
It can establish this ‘tunnel’ by using any third party or untrusted network such as the internet.
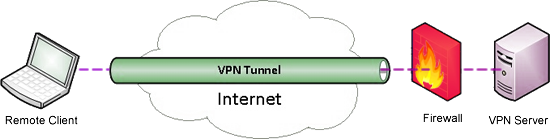
Unlike other paths through the internet, information which passes through this ‘tunnel’ can be encrypted to protect it from inspection or modification.
 VPN concepts for an open network
VPN concepts for an open network
Some parts of the Internet are much more dangerous than others. Public wi-fi connections in cafes, hotels, airports can allow your data to be intercepted and your movements to be tracked. Some countries also routinely monitor all Internet traffic as it enters or leaves the country as well as internal traffic.
A VPN service can offer a VPN client to run on your computer, and VPN servers at safe locations around the world - providing a secure gateway onto the Internet.
When you connect with your VPN client to a VPN service an 'encrypted tunnel' connects your computer to the remote VPN server. It appears to the outside world as though your own computer is located at the VPN exit point in another country.
 VPN concepts for a personal private network
VPN concepts for a personal private network
It is quite possible to install VPN server software on your own private computer at home, and leave it running when you are away from home.
A VPN client software on your mobile device connects to your own home VPN server.
An encrypted tunnel connects your mobile device wherever you are and gives you secure access to your home computer.
To the outside Internet it appears as though you are accessing the Internet from home.
 History
History
VPNs are not a new concept.
Microsoft developed the idea in 1996 to allow employees to access the tech giant's network remotely.
VPNs are now standard in nearly every organization, and growing steadily as a security resource for individual internet users and networks worldwide.
 Why Hide an IP address?
Why Hide an IP address?
These days, everyone from governments to advertisers are after your data, and plenty of people—including your ISP—might be willing to sell it.
Bad actors will also sell your IP address on the dark web so other bad actors can access your devices as well.
Once on your device, hackers can track all of your information including stored passwords, financial information, and accounts of all kinds.
Some journalists and political activists rely on VPN services to circumvent government censorship and safely communicate with the outside world. Check the local laws before using a VPN in China, Russia, or any country with repressive internet policies. Another place people might want to use a VPN is in a war zone such as Ukraine, where hiding locations might well be a matter of life and death.
 How a VPN works
How a VPN works
A VPN is a service that encrypts data and hides your IP address.
The VPN path (or tunnel) between the VPN client and the VPN server relies on encryption to protect the data from interception or modification as it travels across the internet. Encryption turns recognizable information into a garbled collection of unreadable code for anyone who doesn't have a key to decode it. The only entities who hold these keys are your device and your VPN provider. For everyone else your information is unreadable.
In a VPN, encryption and decryption is typically performed by the client and server software. Early VPN solutions used proprietary encryption techniques, but shortcomings in many of these methods has forced a switch to public encryption standards.
Once in place, a VPN should not affect the quality of your online activities in any way.
 Authenticity and integrity
Authenticity and integrity
It is vital to ensure that information can be trusted – that it is coming from an authenticated user and that it has not been altered in transit.
VPNs use a number of methods to ensure authenticity:
 hashes
hashes
 digital signatures
digital signatures
 message authentication codes (MACs) - MACs are appended to messages and act as an authenticator. They are similar in principle to digital signatures, but the hash is encrypted and decrypted using the same secret key (i.e. using symmetric encryption).
message authentication codes (MACs) - MACs are appended to messages and act as an authenticator. They are similar in principle to digital signatures, but the hash is encrypted and decrypted using the same secret key (i.e. using symmetric encryption).
 VPN protocols
VPN protocols
There are three main forms of VPN protocol currently in use (and an open source one):
 PPTP (Point to Point Tunnelling Protocol)
PPTP (Point to Point Tunnelling Protocol)
PPTP was designed in a consortium led by Microsoft, which included an implementation of the protocol as a standard component of Windows NT 4. Microsoft also released PPTP as a free add-on to Windows 95 and Windows 98, allowing users of (at the time) the most popular version of Windows to access corporate networks. PPTP proved unsuited to large companies (being limited to 255 connections per server), but more seriously, the PPTP standard did not settle on a single form of user authentication or encryption; therefore two companies could offer software supporting PPTP, yet each product would be incompatible with the other! From Windows 2000 onwards, Microsoft replaced PPTP with L2TP (see below).
 L2TP (Layer 2 Tunnelling Protocol)
L2TP (Layer 2 Tunnelling Protocol)
This is an adaptation of a VPN protocol known as L2F originally developed by Cisco to compete with PPTP.
In an attempt to improve L2F, a successor was devised by a group composed of the PPTP Forum, Cisco and the Internet Engineering Task Force (IETF). L2TP combines features of both PPTP and L2F.
 IPSec (Internet Protocol Security)
IPSec (Internet Protocol Security)
IPSec was designed by an international committee (The Internet Engineering Task Force (IETF)) in 1992 with a first draft standard published in 1995, the revised standard was published in 1998.
IPSec is now the most widely supported protocol with backing from Intel, IBM, HP/Compaq and Microsoft (among others). IPSec has gained a reputation for security thanks to its use of well-known and trusted technologies.
Rather than invent new techniques for encryption, the designers of the protocol built their system on top of existing encryption technologies, which had, in themselves been subjected to intense scrutiny.
 OpenVPN
OpenVPN
This is an Open Source VPN developed in 2004 based on the SSL/TLS protocol. It is designed to be simpler to set up and operate.
More information can be found at: https://community.openvpn.net/openvpn/wiki/OverviewOfOpenvpn#OpenVPNOSS
 What Devices Will a VPN Protect?
What Devices Will a VPN Protect?
A VPN can be used for every device with internet access:
 Personal computers
Personal computers
 Smartphones and devices
Smartphones and devices
 Tablets and laptops
Tablets and laptops
VPNs can be used on all operating systems, including MAC and Windows.
The Limitations of VPNs
VPN services don't protect against every threat.
A VPN can't help if you have downloaded ransomware onto your computer, or if you give up your data in a phishing attack - you therefore need to employ antivirus software, enabling multi-factor authentication wherever available, and using a password manager to create and store unique, complex passwords for each site and service you use.
There are also limitations to how anonymous you can be with a VPN.
Advertisers have many tactics at their disposal to gather data on you and track your movements. These range from online trackers to browser fingerprinting. You should use the anti-tracking features in your browser and perhaps install a dedicated 'ad or tracker blocker' to counter this.
Many VPN services also provide their own DNS resolution system.
Snoopers can monitor DNS requests and track your movements online. Bad actors can also use DNS poisoning to direct you to bogus phishing pages designed to steal your data, so when you use a VPN's DNS system, it's another layer of protection.
 What Are the Benefits of Using a VPN?
What Are the Benefits of Using a VPN?
A virtual private network levels the playing field in a world of ever-increasing, ever-evolving cybercrime targeting both businesses and individuals.
A VPN account instantly and consistently provides:
 More privacy. Your connections cannot be linked to your computer or your identity. You can visit any website and your ISP doesn’t know where you’ve been.
More privacy. Your connections cannot be linked to your computer or your identity. You can visit any website and your ISP doesn’t know where you’ve been.
 Better security. VPN connections are super secure. The network is hack proof and all of your internet activity is encrypted (coded) and unreadable in transit.
Better security. VPN connections are super secure. The network is hack proof and all of your internet activity is encrypted (coded) and unreadable in transit.
 Increased website access. No more blocks or censorship. They can’t prevent you from getting to websites based on an IP address.
Increased website access. No more blocks or censorship. They can’t prevent you from getting to websites based on an IP address.
 Greater anonymity. Your true IP address is hidden. You’re unidentifiable online because you’re constantly using a different IP address, never your own. In fact, it typically looks as if you’re in a different part of the world from where you really are.
Greater anonymity. Your true IP address is hidden. You’re unidentifiable online because you’re constantly using a different IP address, never your own. In fact, it typically looks as if you’re in a different part of the world from where you really are.
 Peace of mind: Knowing you have added an extra tool to your cybersecurity arsenal will give you the confidence to browse, game, and shop online with less fear of being hacked.
Peace of mind: Knowing you have added an extra tool to your cybersecurity arsenal will give you the confidence to browse, game, and shop online with less fear of being hacked.
 Security risks of VPN
Security risks of VPN
 Security of remote machines for a company
Security of remote machines for a company
When a remote machine is part of a VPN it effectively creates a new frontier between the 'secure' corporate network and the internet. This remote machine now offers a direct route into a corporate network.
It had been relatively simple to secure machines based within a corporate network's offices, but now a 'remote user' might be using their own computer, a network connection, and operating system and software – none of which are 'controlled' by the organisation.
Worse still, they might be sharing the machine with a number of other users, some of which might not even be employed by the organisation!
It is not uncommon for the same PC is used to manage corporate documents - and be used for downloading pirated music from the internet and playing video games!
The remote machines must themselves be secured from abuse - to protect the security of the company network. This involves enforcing minimum standards with regards to operating system, antivirus software, firewalls and so on. Employers need to stipulate that antivirus software is kept up to date, and that all patches and service packs are installed as soon as issued.
It might also be prudent to severely limit what a remote user can access on the internal corporate network when connecting over a VPN.
 Security of the VPN implementation
Security of the VPN implementation
Protocols themselves might be well designed and apparently secure, but the method of implementation, where programmers have taken shortcuts or offered 'additional convenience' to the user, may compromise the protection offered.
For instance, there are no major problems with the PPTP protocol, but Microsoft's implementation of PPTP was found to have a number of serious defects. Microsoft's implementation of PPTP was introduced in 1996, and hacker software exploiting weaknesses began circulating the following year.
Papers describing the weaknesses appeared in 1998, it was only after publication that Microsoft addressed the most serious weaknesses in PPTP by releasing a patch, and even then some issues remained unresolved.
In addition to errors in protocol implementations, security vulnerabilities can be introduced if the design or configuration of the overall VPN solution is done incorrectly.
Security of inter-operation VPN is a technology with a number of competing standards, often supported by different vendors. Mixing and matching hardware and software might cause problems.
Until the technology matures, it might be necessary for a company to use a single technology provider to ensure the software meshes properly.
 How to get a VPN
How to get a VPN
Getting a VPN is as simple as finding a provider and package that suits your needs. Some considerations for making your choice include:
 Multiple device VPN capabilities: All your devices should be covered under one subscription
Multiple device VPN capabilities: All your devices should be covered under one subscription
 Fees: While some services are free, the better VPN providers will be subscription-based
Fees: While some services are free, the better VPN providers will be subscription-based
 Company location: Not necessarily the geophysical location of the company, but the company’s jurisdiction and applicable local data retention laws
Company location: Not necessarily the geophysical location of the company, but the company’s jurisdiction and applicable local data retention laws
 Internet speed: The VPN shouldn’t significantly affect your connection speeds or create lags when in use. Free VPN services are available but tend to be quite slow.
Internet speed: The VPN shouldn’t significantly affect your connection speeds or create lags when in use. Free VPN services are available but tend to be quite slow.
 Trustworthiness: Do your research and read reviews of your VPN choices before committing to a contract
Trustworthiness: Do your research and read reviews of your VPN choices before committing to a contract
 Robust encryption: Look for AES-256 level encryption, widely considered the “gold standard”
Robust encryption: Look for AES-256 level encryption, widely considered the “gold standard”
 Privacy policies: The provider should not keep records of your activities while using the VPN. If personal security is particularly important take care to use a service that doesn’t log user data in any way. ProtonVPN is an example of such a service https://protonvpn.com/.
Privacy policies: The provider should not keep records of your activities while using the VPN. If personal security is particularly important take care to use a service that doesn’t log user data in any way. ProtonVPN is an example of such a service https://protonvpn.com/.
 DNS security: The VPN should protect against Domain Name Server leaks to your ISP provider
DNS security: The VPN should protect against Domain Name Server leaks to your ISP provider
 Killswitch: Automatically blocks devices from connecting to unprotected and unverified sources
Killswitch: Automatically blocks devices from connecting to unprotected and unverified sources
Most VPN providers offer free trials. Take advantage of these trials to make sure the services promised are what you need before signing on the dotted line.

