Cyber Security:
 Two-Factor Authentication
Two-Factor Authentication 
 Dr Seuss and you both know that 'you are you'.... and no one else is 'youer than you', but sadly there are people out there that want to make out they are you - to defraud you.
Dr Seuss and you both know that 'you are you'.... and no one else is 'youer than you', but sadly there are people out there that want to make out they are you - to defraud you.
Authentication is the process or action of proving or showing something to be true, genuine, or valid. In cyberspace it is the process or action of verifying the identity of a user or process.
Having to provide two pieces of information to authenticate a transaction is certainly more secure than simply having to provide one password.
Two-factor authentication has been used for some time. When you withdraw funds from an ATM you have to give the bank two pieces of information – the first is the data stored on your bank card and the second is the PIN.
Individually, neither the card or the PIN can access your account, but when brought together they allow you to withdraw money.
Banking card reader
 Some banks have given similar two-factor authentication to online banking customers – in this case accounts need to be unlocked with the combination of a password and a four or six digit number generated on a hardware banking card reader.
Some banks have given similar two-factor authentication to online banking customers – in this case accounts need to be unlocked with the combination of a password and a four or six digit number generated on a hardware banking card reader.
(If you use online banking and don't have a card reader device it will be well worth finding out if your bank offers them to customers, and if they do not, consider switching to a more secure banking service).
The banking card reader reads the account details from your bank debit card, which includes your account number and a hash of your pin.
It will require you to enter your pin to log in, and if the pin matches the hashed pin it has read from your card, the reader then generates a passcode that can be used on the banks website to authorise log in and certain transactions.
The banking card reader confirms that you physically have the card and that you know the pin, and you can get authorisation without needing to enter a pin on a web page.
 Two-factor authentication (2fa) on the internet
Two-factor authentication (2fa) on the internet
 A number of online companies, including Apple, eBay, Google and Microsoft support two-factor authentication to improve the security for their web users.
A number of online companies, including Apple, eBay, Google and Microsoft support two-factor authentication to improve the security for their web users.
Rather than a single password, two-factor authentication requires the user to enter two pieces of information – their password and a changing value which is either sent by the website to their mobile phone, or generated by a companion application on the user's own computer.
Depending on the site, it might be necessary to enter the two values every time (which can be inconvenient), or after a period of inactivity, or it may be possible to tell the site that the computer which has already been authenticated should be trusted in future and a single password will be sufficient to allow you to use the site (although this raises a security weakness if the machine should be stolen).
 This method of two-factor authentication works well as protection against random attacks.
This method of two-factor authentication works well as protection against random attacks.
Two-factor authentication is available on many websites and it's very easy to set up. Follow the instructions on their webpage to add two-factor authentication to your accounts.
You need to make sure that you check how you could log in if, for some reason, you didn't have access to your phone or phone signal, especially if you lost your phone or had it stolen.
 Two-factor authentication on Google
Two-factor authentication on Google
If you have a Google account it is a good idea to set up two-factor authentication. Google's two-factor authentication sends authentication codes to your mobile phone. You will need a phone that only you have access to, as otherwise someone who has stolen your details could use it to gain access to your Google account.
 Two-factor authentication on Facebook
Two-factor authentication on Facebook
Facebook also supports two-factor authentication (which it calls Log in Approvals). Facebook's two-factor authentication process is activated whenever you log in from a new computer. An SMS is sent to your phone containing a unique security code, which you will need to enter into Facebook before you can log in.
Other two-factor authentication services
As well as many online banking systems, other websites support two-factor authentication, most of which rely on SMS messages or a security authenticator app as second verification of your identity.
Such services include: 
 Apple
Apple
 Dropbox – a cloud file sharing service
Dropbox – a cloud file sharing service
 Evernote – a cloud-based document and note taking service
Evernote – a cloud-based document and note taking service
 Microsoft Accounts – access to multiple services including the OneDrive cloud storage service, and purchases from the Microsoft App Store - SMS and also its ownAuthenticator App.
Microsoft Accounts – access to multiple services including the OneDrive cloud storage service, and purchases from the Microsoft App Store - SMS and also its ownAuthenticator App.
 PayPal – online payments used by many small web retailers and eBay
PayPal – online payments used by many small web retailers and eBay
 Steam – online game delivery
Steam – online game delivery
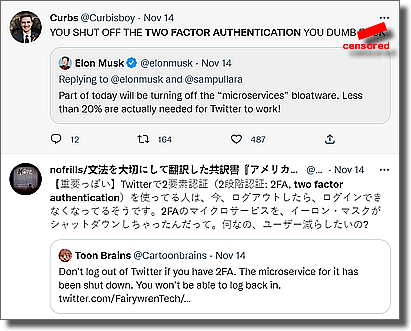
 Twitter did have 2FA - but when Musk messed with the system in November 2022 those who had 2FA (and needed a SMS code to authenticate themselves) couldn't get back in!
Twitter did have 2FA - but when Musk messed with the system in November 2022 those who had 2FA (and needed a SMS code to authenticate themselves) couldn't get back in!
 How to stop your phone being hacked
How to stop your phone being hacked
If you are being specifically targeted by an attacker, criminals have found it quite easy to take over a user's phone number and then intercept or initiate authentication messages.
They don't even need to steal the phone to do this.
They can easily can locate your telephone number and date of birth on social media accounts, and then ask for the number to be transferred to a new sim with a new provider. They have then cloned your phone!
To greatly reduce this risk:
 Use a dual sim phone with a number on a pay-as-you-go tariff where the balance remains indefinitely – you usually have to make one call every six months to keep the sim working. Only use that number for two-factor authentication, not for anything else and never publish that number.
Use a dual sim phone with a number on a pay-as-you-go tariff where the balance remains indefinitely – you usually have to make one call every six months to keep the sim working. Only use that number for two-factor authentication, not for anything else and never publish that number.
OR
 Use a separate very basic phone or an old phone with a new pay-as-you-go sim purely for authentication, only switching it on when you want to get an authentication. Don't used this phone for making phone calls and never publish the number anywhere.
Use a separate very basic phone or an old phone with a new pay-as-you-go sim purely for authentication, only switching it on when you want to get an authentication. Don't used this phone for making phone calls and never publish the number anywhere.
If your mobile phone number stops working contact your phone provider immediately to check why - It might have been diverted.

 Use a hardware security key
Use a hardware security key
Using a hardware security key on a computer is a much more secure method of two-factor authentication than using your phone.
It restricts authentication to the computer with a unique hardware security key that uses your fingerprint to access your account and prove you are you!
You have to set it up and then be careful not to lose it - or leave it in a computer! (At work it is best to have it attached to a chain on your belt - so if you try to walk away it will not let you!).
To access an account you activate 2FA, and then enroll your security key as one of the options of improved security offered by the company. Then any future logins will require your username, password and security key.
However, although they have been around for several years, not that many sites allow the use of a security key - and force you to use an SMS message or authenticator app.
The list of sites on Yubico's website is extensive, but it include sites that use the Yubico authenticator app.
The Yubico authenticator app is allows tokens using your Yubico Yubikey but the fact you have to use an authenticator app is defeating the purpose of having the Security Key.
Some sites force you to sign up to SMS 2FA backup or download backup codes.

 Two-Factor Authentication
Two-Factor Authentication  Dr Seuss and you both know that 'you are you'.... and no one else is 'youer than you', but sadly there are people out there that want to make out they are you - to defraud you.
Dr Seuss and you both know that 'you are you'.... and no one else is 'youer than you', but sadly there are people out there that want to make out they are you - to defraud you. Some banks have given similar two-factor authentication to online banking customers – in this case accounts need to be unlocked with the combination of a password and a four or six digit number generated on a hardware banking card reader.
Some banks have given similar two-factor authentication to online banking customers – in this case accounts need to be unlocked with the combination of a password and a four or six digit number generated on a hardware banking card reader.  A number of online companies, including Apple, eBay, Google and Microsoft support two-factor authentication to improve the security for their web users.
A number of online companies, including Apple, eBay, Google and Microsoft support two-factor authentication to improve the security for their web users.  This method of two-factor authentication works well as protection against random attacks.
This method of two-factor authentication works well as protection against random attacks.




