Cyber Security:
 Phishing
Phishing 

 Phishing is any attempt by attackers to steal valuable information by pretending to be a trustworthy party.
Phishing is any attempt by attackers to steal valuable information by pretending to be a trustworthy party.
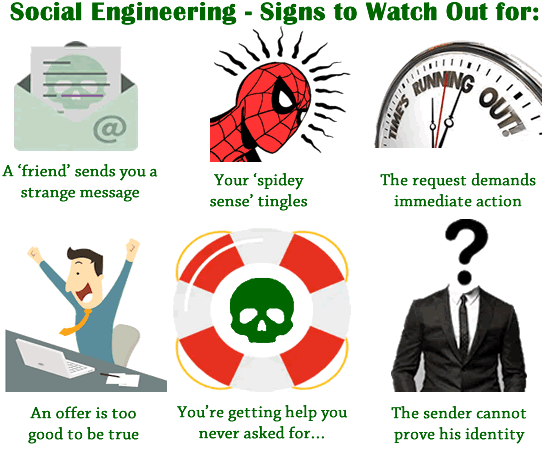
It is a form of social engineering attack - a form of exploiting your human weaknesses so you let your guard down. You need to be alert and cautious when using your computer, tablet or smartphone, and when responding to snail mail or telephone calls.
It gets its name from 'fishing' – as in 'fishing for information', the process of luring people to disclose confidential information. The term "phishing" is said to have been coined by the well known spammer and hacker in the mid-90s, Khan C. Smith. When fishing you dangle bait on a hook and wait patiently for the fish to 'bite'. That is what 'phishers' do - they exploit human weaknesses - so that phishers can 'hook' their victims.
A 'phisher' might impersonate a bank official to obtain credit card numbers or bank account details, or pretend to be an IT person at a shopping site.
Phishing relies on people trusting official looking messages, or conversations with apparently authoritative individuals. They do not double check as they think they seem genuine - and fear being thought of as rude or over-anxious by checking. It is widespread crime and it can be enormously costly to people who find their bank accounts emptied, credit references destroyed or lose personal or sensitive information.
 Cyber security breaches do not occur in the main because of 'technical failures'. 'Social engineering' is the main cause of criminals gaining access to computer systems. Attackers exploit the goodwill and trust of people, especially of people they think are in positions of trust, to obtain access to their accounts.
Cyber security breaches do not occur in the main because of 'technical failures'. 'Social engineering' is the main cause of criminals gaining access to computer systems. Attackers exploit the goodwill and trust of people, especially of people they think are in positions of trust, to obtain access to their accounts.
 A telephone call from someone pretending to be an engineer from 'technical support' or getting an e-mail that asks for confirmation of usernames and passwords are common ways in which criminals make 'social engineering attacks'.
A telephone call from someone pretending to be an engineer from 'technical support' or getting an e-mail that asks for confirmation of usernames and passwords are common ways in which criminals make 'social engineering attacks'.
 E-mail phishing
E-mail phishing
Phishing emails can use your real details and passwords to make you think that the attacker is a real contact that you already know, or to make you think that they have more information than they actually do to panic you into clicking on a message.
 The use of electronic technologies to perform phishing attacks was described in the late 1980s, but the term did not become commonplace until 1995 when a program called AOHell allowed AOL users to impersonate other people (including the founder of AOL itself). The program included a fake account generator which would generate a new, fully functional AOL account for the user that lasted for about a month and a "fisher" tool that enabled hackers to steal passwords and credit card information through automated social engineering.
The use of electronic technologies to perform phishing attacks was described in the late 1980s, but the term did not become commonplace until 1995 when a program called AOHell allowed AOL users to impersonate other people (including the founder of AOL itself). The program included a fake account generator which would generate a new, fully functional AOL account for the user that lasted for about a month and a "fisher" tool that enabled hackers to steal passwords and credit card information through automated social engineering.
The program would barrage random AOL users with instant messages like:
'Hi, this is AOL Customer Service.
We're running a security check and need to verify your account.
Please enter your username and password to continue'.
Phishing became increasingly common during the next decade as it became clear how easy it was to fool people who had trust in officials. Also it became easier to copy digital information, logos and text styles - so the fakes looked very much like the official ones.
More and nore people began receiving 'official looking messages' - very similar those sent out by genuine organisations such as banks, stores and government departments.
Click here for further advice on spotting a phishing e-mail.
Phishing emails may be indiscriminate (casting a big, wide net) - a phisher may create an email asking the user to get in touch with a bank or credit card company claiming that there is a problem with the account. The phisher will then include some plausible looking details such as a bank's logo and address and then send it to millions of individuals. Among all the recipients, only a small percentage will have accounts with that particular bank and will click the link in the message, or ring a telephone a number, which will begin the process of eliciting further personal information.
E-mail attacks may also be 'spear phishing' (see below) - aimed specifically at an individual - not casting a wide net. To do this depends on the attacker having detailed information about the target. For example, an attacker might use information gleaned from recent e-mails to craft a plausible 'reply/comment' that appears to come from colleagues of the targeted user. Attackers may then include links to malware-infected software in the e-mail - or a bogus telephone number - or simply ask for sensitive information to be sent to them.
 What to do if you suspect an e-mail phishing attack
What to do if you suspect an e-mail phishing attack
If you get an e-mail that 'worries you':
 do not click on or follow the links in the message.
do not click on or follow the links in the message.
 contact the customer services department (looking up the details from the web - not using details on the e-mail).
contact the customer services department (looking up the details from the web - not using details on the e-mail).
 log in to your account through their website.
log in to your account through their website.
 report the 'phish'.
report the 'phish'.
 Be prepared for a phishing attack
Be prepared for a phishing attack
In your address book, type:
 web addresses of favourite sites
web addresses of favourite sites
 published phone numbers of companies you deal with.
published phone numbers of companies you deal with.
 published policies concerning asking for sensitive information such as your password through email or over the phone. Most say they will never do that! So you should be suspicious of anything that contravenes this policy.
published policies concerning asking for sensitive information such as your password through email or over the phone. Most say they will never do that! So you should be suspicious of anything that contravenes this policy.
 where to forward suspected phishing attacks for organisations you deal with
where to forward suspected phishing attacks for organisations you deal with
 Online database breaches
Online database breaches
The criminals often get your email address and password data etc. from the many breaches of online databases that occur. They then try to 'dupe' you.
 Why you should always report phishing scams
Why you should always report phishing scams
 The National Cyber Security Centre (NCSC) is a UK government organisation that has the power to investigate and take down scam email addresses and websites.
The National Cyber Security Centre (NCSC) is a UK government organisation that has the power to investigate and take down scam email addresses and websites.
Reporting a scam is free and only takes a minute.
By reporting phishing attempts, you can:
 reduce the amount of scam communications you receive
reduce the amount of scam communications you receive
 make yourself a harder target for scammers in the furture
make yourself a harder target for scammers in the furture
 protect others from cyber crime online.
protect others from cyber crime online.
 Spear Phishing
Spear Phishing
Spear phishing is targeted towards a specific individual, organisation or business.
The cybercriminal may intend to:
 steal data for malicious purposes and/or
steal data for malicious purposes and/or
 install malware on a targeted user's computer.
install malware on a targeted user's computer.
 How 'Spear Phishing' is carried out:
How 'Spear Phishing' is carried out:

 An email arrives - apparently from a trustworthy source, but instead it leads the unknowing recipient to a bogus website full of malware.
An email arrives - apparently from a trustworthy source, but instead it leads the unknowing recipient to a bogus website full of malware.
 Clever use of individually designed approaches and social engineering techniques are employed - effectively personalising messages and websites.
Clever use of individually designed approaches and social engineering techniques are employed - effectively personalising messages and websites.
As a result, even high-ranking targets within organisations, like top executives, can find themselves opening emails they thought were safe and enabling cybercriminals to steal the data they need in order to attack the organisation's network.
 See here for examples of spear phishing.
See here for examples of spear phishing.
 Social media phishing
Social media phishing
The techniques used in e-mail phishing are also used in a social media site phishing venture.
The same rules on being cautious apply – if in doubt, go to the official site and make contact with the company through their published links.
Social media phishing is generally targeted at individuals - in other words employing 'spear phishing'.
To do this effectively depends on the attacker having detailed information about the target - and social media pages are full of information - within post content, comments and links made by friends and from photos that are published. Quite a dossier on an individual can be built up in a very short time!
Attackers may include links to malware-infected software in personal messages posted in social media - or in text messages. This is especially common after major disasters or during fast-breaking news when people are likely to click on interesting looking links without thinking carefully.
Some people put their e-mail address and phone number up on a social platform making it really easy for 'phishermen' to phish their via phone or their e-mail accounts. Armed with a lot of background information so that they can craft a really good specifically targeted scam via e-mail.
 So think before you share....
So think before you share.... 
Phishing is also a type of spam email which slows down servers, contributes to global warming, and clutters up our mailboxes - delivering unsuitable and sometimes illegal content or malware to individuals.

 Phishing
Phishing 



 Why you should always report phishing scams
Why you should always report phishing scams  The
The 


