Cyber Security:

Risk Analysis
 Risk can be thought of as the chance of adverse consequences or loss occurring. Risks can be identified and the likelihood of them occurring assessed in risk analysis.
Risk can be thought of as the chance of adverse consequences or loss occurring. Risks can be identified and the likelihood of them occurring assessed in risk analysis.
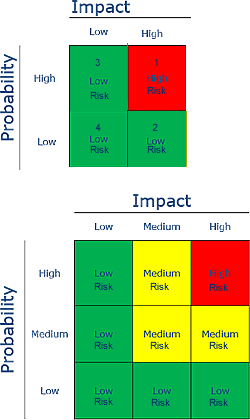
The main technique for a qualitative analysis of risk is to construct a likelihood–impact matrix in which the likelihood and impact of each risk event are assessed against a defined scale and then plotted on a two-dimensional grid.
The position on the grid represents the relative significance of each risk. The simplest matrix is formed by classifying both likelihood and impact as either high or low, which leads to a 2 by 2 grid.
This basic classification of a high or low value leads to the following rank order for tackling risks:
- high-impact, high-likelihood risks
- high-impact, low-likelihood risks
- low-impact, high-likelihood risks
- low impact, low-likelihood risks.
Low-impact, low-likelihood risks are probably not worth expending much effort on.
You need to prioritise the high-impact and high-likelihood risks one by one to determine whether there are ways either to reduce the impact if the risk occurs or to reduce the likelihood of the risk occurring, or both.
The next stage is to apply quantitative techniques, based on a financial assessment of the impact of each of the risks, to put the risks into order, with the greatest risks at the top of the list.
Sometimes it is hard to reach a decision about the importance of some risks until a corresponding response has been identified as well as any possible interactions between risk events and responses, so risk management is usually iterative in practice.
 Example
Example
Let's do a risk assessment of what would happen if personal assets were attacked by a hacker.
 study materials – documents and data relating to school/university studies
study materials – documents and data relating to school/university studies
 digital photographs – images taken since digital cameras became the norm in the 1990s
digital photographs – images taken since digital cameras became the norm in the 1990s
 music – tracks ripped from CD or bought online
music – tracks ripped from CD or bought online
 movies – digital copies of films and TV programs bought
movies – digital copies of films and TV programs bought
 e-mail – online correspondence (both personal and dealings with employers and companies you have purchaced goods/services from)
e-mail – online correspondence (both personal and dealings with employers and companies you have purchaced goods/services from)
 banking and other financial records
banking and other financial records
 passwords and account details
passwords and account details
Carefully go through each and decide the impact loss would have - and the probability of them being targeted by hackers...
1. E-mail, banking details and password information would have high impact and there is a high likelihood that these would be targeted by a hacker due to their high value.
2. The study materials or digital photographs would have high impact, but there is a low likelihood given that these assets have minimal financial value to an attacker.
3. An attack on digital music or videos would have low impact, since these can be downloaded again easily. However, this will have high likelihood because these assets can be easily copied and sold, this making these attractive to an attacker.
This then gives you an order of action in which to protect your assets.


 Risk can be thought of as the chance of adverse consequences or loss occurring. Risks can be identified and the likelihood of them occurring assessed in risk analysis.
Risk can be thought of as the chance of adverse consequences or loss occurring. Risks can be identified and the likelihood of them occurring assessed in risk analysis.
 Example
Example 

