The video below explains how data is routed across a network of computers and how the internet is resilient to failures of individual computers (known as 'nodes of the network'), or connections between computers (known as the 'links').
Instead of using a dedicated circuit route for all of the information, internet traffic is split up and may take any number of routes through the network moving from its origin to the destination by a series of hops. (Rather in the way Amazon sends out packages - using 'hubs that have less traffic' - even if further away - to speed up delivery of a package).
The internet is made up of thousands of separate networks owned by governments, corporations, and individual users.
The computers and links that make up the internet are built by a huge number of companies, and use a large range of different technologies to store and transmit information.
The internet is made possible, because although there are a large number of different types of computer and networking equipment, they all understand a relatively small number of communications protocols.
'Communications protocols' are formalised in digital rules that allow different networks and differing communications equipment to talk to one another known as for internet data transfer the two most important are:
- the Transmission Control Protocol (TCP), and
- the Internet Protocol (IP).
They are so inextricably linked that they are often written together as TCP/IP.
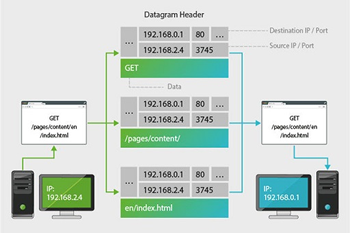
Before data can be sent across the internet, the TCP is used to break it into fixed-size chunks - known as datagrams - or 'packets'.
Each datagram contains:
a small amount of data
information needed by the internet itself:
the addresses of both the sender and the recipient
a serial number.
The addressed 'datagrams' are passed by the sender's computer to a nearby router, (such as one on their home network).
Between them, TCP and IP offer an extremely reliable way of sending data over what might be an unreliable network.
Protocols
| TCP |
Transmission
Control
Protocol |
Provides a structure for reliably sending data over a network. (TCP is not responsible for sending and receiving information - just the structure)
It works through a number of software ports that act to keep data separate on the same computer – so it is possible to browse a web page, collect email and listen to streaming music at the same time.
PORTS
To understand how TCP works you need to know something about ports.
A port can mean different things depending on the context.
A port can be a physical connection on a device such as the USB port into which you plug your printer or flash drive.
But for TCP, it means a number which indicates how data is handled when it reaches its destination.
Many ports represent specific protocols such as port 80 representing the well-known port of HTTP.
Common TCP ports include the following:
| port 20 and 21 |
– File Transfer Protocol (FTP) for sending and receiving files (port 20) and control (port 21) |
| port 22 |
– Secure Shell (SSH) for secure logins to computers |
| port 25 |
– Simple Mail Transfer Protocol (SMTP) for sending email |
| port 80 |
– HyperText Transfer Protocol (HTTP) for browsing web pages. |
Data being sent from an application on your computer is divided into TCP datagrams each containing the TCP port number.
The TCP application running on the recipient's computer will then examine this port number to determine which application should receive the information in the datagram.
TCP’s second major task is ensuring that all data sent from a computer is received by its destination.
It waits for acknowledgements from the remote computer, and in the event that a datagram gets lost or damaged in transit, it can resend the missing datagram.
For this reason TCP is reliable – but relatively slow.
Applications where timeliness is more important than absolute accuracy – such as streaming media, video games and video conferencing – will use less reliable, but faster, protocols such as UDP (User Datagram Protocol) to send and receive their data.
If you are receiving an email, you want the whole message to arrive with no gaps, but if you are streaming a TV programme, it doesn’t greatly matter if a few datagrams get lost.
Final destination
When datagrams finally reach their destination, TCP is responsible for restoring the data to its original condition.
The serial numbers on each datagram allow them to be ordered so that the data can be correctly reconstructed.
TCP also allows the receiver to request new copies of missing or damaged datagrams from the sender. |
| IP |
Internet
Protocol |
Used to transmit information across the internet.
IP is only concerned with moving data, it doesn't actually check that data actually arrives (that's handled by TCP).
When IP receives data from TCP to be sent on to the internet it wraps the TCP datagram in its own IP datagram containing a sender's and a receiver's address as well as some other information.
When IP receives data from the internet, it removes the IP datagram information and passes it to TCP which will perform the checking of the contents and reordering of information before it can be passed through the appropriate port to an application.
IP addresses
The internet addresses used by humans (such as www.cybercomputing.co.uk) are purely for our convenience, as computers use numeric addresses known as 'Internet Protocol' addresses (or IP addresses, or sometimes IP numbers) for communication.
Every computer directly connected to the internet has a unique Internet Protocol (IP) address.
There are two major forms of IP address:
IPv4 (Internet Protocol version 4)
This is the most familiar form of IP address consisting of four numbers, each ranging from 0 to 255, separated by full stops (periods) in the form 192.168.0.1.
IPv4 has long underpinned the internet although it is now in urgent need of replacement because the number of devices connected to the internet has nearly exhausted the total number of available IPv4 addresses.
IPv6 (Internet Protocol version 6)
IPv6 is a a replacement for IPv4, originally outlined in 1998, to accommodate the increasing demand for IP numbers as more people and devices were connected to the internet.
It can support a theoretical 3.4×1038 devices meaning it is suitable for any conceivable demand.
IPv6 is intended to replace IPv4; however this is an extremely complex process and it has taken a long time with even the most developed countries still far from completing the transition.
A measure of compatibility exists in the form of IPv4-mapped IPv6 addresses where IPv4 addresses are stored in the IPv6 format.
Reserved IP numbers
Not all of the numbers in the IPv4 address range are actually available for use.
As well as large blocks reserved for specific users in the early days of the internet, some are specifically used for 'private' networks outside of the internet.
10.0.0.0 to 10.255.255.255
169.254.0.0 to 169.254.255.255 (computers unable to connect to a local network)
172.16.0.0 to 172.31.255.255
192.168.0.0 to 192.168.255.255 (home computers connected to a network hub has a genuine IP address, your computer and other devices attached to the modem each have private addresses.)
Your modem alters IP addresses on packets as they are sent to and from your home network and the internet. |
Networks
Since all of our computers understand the same protocols, it appears that they all belong to the same network. But the internet is made up of a hierarchy of networks all communicating through TCP/IP.
Tier |
Hosted By |
Infrastructure |
Tier one
- sometimes called the internet backbone - principal data routes between large, strategically interconnected computer networks and core routers of the Internet. |
These data routes are hosted by commercial, government, academic and other high-capacity network centers, as well as the Internet exchange points and network access points, that exchange Internet traffic between the countries, continents, and across the oceans.
Some Internet service providers, participate in Internet backbone traffic by privately negotiated interconnection agreements, primarily governed by the principle of settlement-free peering. |
Undersea Internet optical fibre cables serve as the physical infrastructure of the Internet.
|
| |
Telecommunication companies who own the all-important cables that allow data to travel around the world. |
Optical cables |
| |
Internet service providers or corporate networks who provide high speed access to internet services via wifi |
Wi-Fi |
| lowest tier |
Made up of individual users, who might be connected together by wifi in a local area network. |
Wi-fi |
Routers
Routers work rather like a Post Office sorting office.
Each datagram is sent through a series of computer nodes that form the backbone of the Internet.
There are many thousands of these nodes and often many different routes between them.
Each of these nodes has an IP address.
If you look up the IP address of the node using ‘whois’, some will provide a geographical location for the node.
Some will provide only the country of that node, and some provide no location information.
See the page on IP Addresses to find out how to track routes.
local delivery |
Your local router extracts the destination address of the datagram, and looks for that destination in a table of known addresses. If the destination address is known to the router, then the datagram is sent to the destination computer. |
This corresponds to you sending a letter and the local Post Office recognising that the postcode indicates the letter is within its area for local delivery. |
outside the area |
However, if the destination address isn't known to the router, it forwards the datagram to a higher-level router, which has a more comprehensive list of addresses. A datagram might be forwarded all the way up to the routers on the internet's backbone. |
This is equivalent to sending the letter to a large district sorting office. |
sending between district sorting offices |
The higher-level routers only need to examine the first part of the destination address to determine where the datagram needs to be forwarded.
Once its address is found in a router's address table, the datagram can be redirected to a lower-level router, which will in turn forward it to more and more local routers until it eventually reaches its destination. |
Once in the correct major area sorting area the letter can be sent to the correct local sorting office - and from there to a Postman's delivery route. |
| |
|
|
Routers constantly inform one another about their status and how busy they are.
When parts of the internet become congested, or the router becomes unavailable, other routers will find new paths for datagrams that to avoid the problem.
IP's ability to constantly reroute data to ensure a reliable flow of traffic means it's entirely possible for datagrams containing parts of the same file to take completely different routes across the internet.
Converting a web-address into an IP address
When we type an address (such as www.cybercomputing.co.uk) into a browser, the address is translated into a unique IP address by a name server, called a Domain Name Server (DNS), located somewhere on the internet.
This IP address is attached to every IP datagram destined for the cybercomputing server.
As an example we will consider an IP datagram belonging to an email being sent to Johnny who works in the coffee bar at Big University in America (Johnny’s address is johnny@coffee.big.edu).
The address is sorted from the most general part of the address to the most specific:
- The name server on the sender’s machine makes a request across the internet to a computer which holds the addresses of all American universities (most of which use .edu at the end of their address) asking for the IP number of big.edu.
- The .edu name server responds with the IP number for the name server at Big University.
- The sender’s machine then uses that IP number to make a link to the name server at Big University and requests the IP number of the coffee shop computer used by Bob.
- The big.edu name server responds with the address of the coffee shop.
- The IP datagrams can then all be addressed correctly and sent into the network.
Up until 2019, the DNS information requested was sent as plain text and could be intercepted even when the data being sent or requested was encrypted.
From 2019, it has become possible for DNS requests to be encrypted on browsers





