Cyber-Security:
A brute-force attack can, in theory, be used to attempt to decrypt any encrypted data (except for data encrypted in an information-theoretically secure manner). It runs rather like you see in 'War Games' when the protagonist leaves his computer on all day, automatically trying a series of codes in order to get into a system. The difference being that nowadays you can try millions of code combinations in a short time! In a simple brute force attack a computer will methodically work through all possible passwords (beginning with ‘A’, then ‘AA’, ‘AB’ and so on …) trying each in turn until it stumbles upon an actual password. The more digits in the password the longer it takes to 'break' - but also the characters used matter. Let us look at the cracking of an 8-digit password:
|
Password contains lower case characters |
Password contains upper case characters |
Password contains numbers |
Password contains special characters |
Time to crack an 8-character password /minutes |
0 |
||||
2 |
||||
7 |
||||
39 |
The above data related to 2017. But with faster processors the time taken to brute force crack a code is diminishing.
In 2020, Hive Systems shared a colourful table that showed the relative strength of a password against a brute force cracking attempt, based on the password's length and complexity. You will find it everywhere on the www.
The data was based on how long it would take a consumer-budget hacker to crack a password hash using a desktop computer with a top-tier graphics card.
Two years later – quite a long period of time in processing power improvement terms – they published an update.
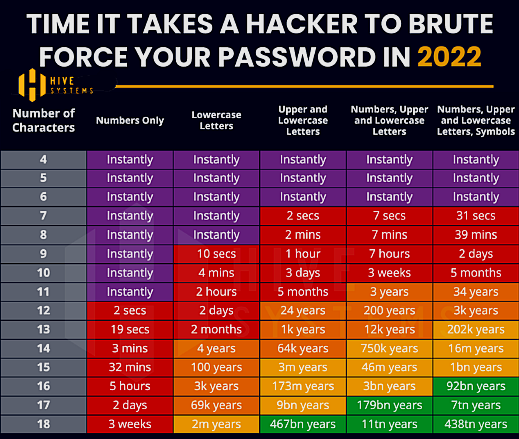
It is evident that to be safe, a password should be complex (upper and lower case letter, numbers and symbols) and as made up of as many characters as possible to be safe.
 Password 'guessing'
Password 'guessing'
The attacker submits many passwords or passphrases with the hope of eventually guessing correctly.
The attacker systematically checks all possible passwords and passphrases until the correct one is found.
Brute-force attacks work by calculating every possible combination that could make up a password and testing it to see if it is the correct password. As the password's length increases, the amount of time, on average, to find the correct password increases. Longer passwords, passphrases and keys having more possible values, make them exponentially more difficult (and take more time) to crack than shorter ones.
This method is therefore very fast when used to check all short passwords, but for longer passwords other methods such as the dictionary attack are used because a brute-force search takes too long.
 Guessing 'the key'
Guessing 'the key'
Alternatively, the attacker can attempt to guess 'the key' which is typically created from the password using a key derivation function to 'hash' the password
This is known as an exhaustive key search.
 Reverse hacking of passwords and keys
Reverse hacking of passwords and keys
Sometimes the hackser have the passwords or keys but do not know who they are associated with. The search to match them can also be done by Brute Force.
 Typical Brute Force Attack Methods
Typical Brute Force Attack Methods
Traditional Attacks: the hacker has a username or list of usernames and attempts, manually or by running a brute force program script, to guess passwords until a correct combination of credentials is found.
Dictionary Attacks: a hacker will attempt to log into an account by working his way through one or more 'dictionaries'. Each entry in the dictionary is a possible password and if it doesn't work, the computer moves on to the next one.
Hybrid Attacks: A method of combining simple (traditional) brute force attacks with dictionary attacks.
The hacker takes the most common phrases and words from the "dictionary" and attempts numerous variations of potential passwords until a combination is found.
Reverse Brute Force Attacks: A method where a hacker starts with a known password, but has no idea who uses it. It has either been acquired from a breach or is a commonly used one. S/he then searches and attempts many usernames until a combination is found.
This is 'reverse' to a traditional brute force or dictionary attack as they are working backwards and starting with the known passwords instead of known usernames.
Credential Stuffing: This is a method where a hacker already has a known username and password combination for one system and uses those same credentials to access other accounts, profiles, or systems associated with the same user.
This attack works because users frequently recycle passwords across their accounts - and is the reason why you should never use the same password for more than one account.
Password spraying: The hacker applies a single password across multiple systems rather than attempting many passwords for one account, application, or network.
 Tools used to make Brute Force Attacks
Tools used to make Brute Force Attacks
These are freely available on the internet. There are many out there - here is a few of the most popular (these even have people on You Tube telling you how to use them!):
John the Ripper: This is an open-source piece of software that lets potential hackers run dictionary attacks and detect weak passwords through various cracking and decryption techniques.
Aircrack-ng: This is an open-source tool that focuses on penetration testing for wireless network security through dictionary attacks against network protocols.
Hashcat: This is 'password recovery tool' that can be used by hackers. It is a penetration testing platform that lets hackers use known "hashes" - a password that has been run through a program that converts to a string of random characters that is always the same length regardless of how much data the password contains.
With the hashes known, they can use Hashcat to run dictionary or rainbow table attacks to reverse the password back to readable text.
 Hardware required to carry out Attacks
Hardware required to carry out Attacks
Any type of use of a software tool to carry out a brute force attack requires a computer system with a lot of memory and processing speed. Therefore powerful hardware is vital.
A single central processing unit (CPU) isn't usually enough to quickly crack a password or even run these functions at all. Therefore those involved in cybercrime industry now employ graphics processing units (GPUs) so as to accelerate data processing tasks.
 Online and Offline Brute Force Attacks
Online and Offline Brute Force Attacks
In online brute force attacks, the hacker directly targets the network or application. However, these attacks are restricted by the system's countermeasures. For instance, most systems will lock a user out after a certain number of incorrect login attempts.
To get around this potential roadblock, attackers can use offline brute force attacks. These attacks enable password key cracking attempts without logging into the user's server.
Since password data uses hashes or encryption for security purposes, the hacker works backward during offline attacks by taking the known hashes and running a computer program to match them up with the known passwords until a correct combination has been found.
 Combatting Brute Force Attacks
Combatting Brute Force Attacks
Dictionary and brute force attacks can be foiled by having computer systems watch for unsuccessful attempts to log in to accounts. Almost all computer systems restrict the number of unsuccessful logins after which the account is locked and can only be accessed after the intervention of an administrator.
Brute force attacks are rooted in credential compromise. So steps must be taken to prevent access via 'slip ups' by employees or users.
Brute-force attacks can be made less effective by 'obfuscating' the data to be encoded, thus making it more difficult for an attacker to recognize when the code has been cracked. Or they can be discouraged by making the attacker do more work to test each guess.
One of the measures of the strength of an encryption system is how long it would theoretically take an attacker to mount a successful brute-force attack against it.
Precautionary operational steps to take:
employees of firms should be required construct complex passwords.
passwords should be changed every few months.
for both external and internal applications, system administrators should incorporate lockout policies that keep potentially malicious actors out of a system after too many incorrect login attempts.
multi-factor authentication (MFA), to require additional authentication should be employed
firms should have up to date anti-virus software on their systems - perhaps investing in the new AI/ML approach to malware infection so that any breach is immediately dealt with - minimising damage.

 Brute Force Attacks
Brute Force Attacks