Cyber-security:
To be 'air gapped' is to be cut off from the public internet. In an air gapped environment, all the usual communication software: email clients, browsers, SSH and FTP clients are disconnected from the outside world. Hackers often scan the public internet for vulnerable machines through services like Shodan.
It has been described as a search engine of 'service banners', which are metadata that the server sends back to the client. This can be information about the server software, what options the service supports, a welcome message or anything else that the client can find out before interacting with the server. It was launched in 2009 by computer programmer John Matherly, who, in 2003, conceived the idea of searching for devices linked to the Internet. The name Shodan is a reference to SHODAN, a character from the System Shock video game series - see the wonderful graphic on the right! But, an air gapped computer has no connection to the internet, so hackers (even using Shodan) cannot get to it. There be no wired connections to other computers or devices unless they are also similarly air gapped. To be truly 'air-gapped' there must be no wifi connection, no Bluetooth, no ethernet cable, no modem - and great care taken so that employees or visitors do not compromise the system by connecting potentially infected hardware to the system.
Even remote code execution (RCE) software bugs cannot be directly exploited by an attacker outside of the air gapped network itself when the computer is so 'cut off'. An air gapped network is one that has no physical connection to the internet and no connection to any other local area network which is not itself air gapped. All devices within the network are invisible to, and effectively isolated from, remote threats. An air gapped system can, of course, communicate with other physically separated devices, but any means of data transfer outside of the network must take place through external hardware, temporarily attached to the network: for example USB flash drives and other removable media as well as specially-authorized laptops. These external devices require a person to physically connect and disconnect them to the air gapped network. Devices which are only partitioned from other network devices by means of a software firewall are not considered to be air gapped, since such software can easily contain vulnerabilities that might allow entry to remote attackers. Advantages & Challenges of an Air Gapped NetworkBeing invisible to attackers searching the public internet for devices vulnerable to remote attacks is a huge security advantage. Hackers wishing to attack such devices unless they do so directly with the device itself or indirectly via compromising another device that may temporarily have physical access. Those who would benefit include:
Challenges with using air gapped systems safely.
For the vast majority of computer tasks, data needs to be uploaded at certain times, and similarly data processed on an air gapped computer or device may need to be transferred elsewhere to make it useful or available to others who need it. It is this transfer of data that presents the greatest risk. Strict procedures need to be in place to prevent employees having a false sense of security that the network is inherently safe because of its lack of internet connectivity. The integrity of the air gap is only maintained when the means of data transport in and out of the environment are equally subject to the highest levels of security. In practice, the integrity of air gapped networks has proved to be extremely difficult to maintain without strict security controls being put in place. How Secure Are Air Gapped Networks?Because of the difficulty of maintaining an effective air gap, it is not surprising that hackers have found ways to attack air gapped computers.
The SolutionThe answer is an on-device behavioral AI that can detect, protect and remediate malware, ransomware and device-based attacks from peripherals like USB drives autonomously. A solution that can operate independently of internet connectivity to detect both known and novel malware based on behavior rather than file identity. These AI solutions are being created at the moment. |
|

Custom Search
 Air Gapped Networks
Air Gapped Networks Shodan is a search engine that detects the use of servers (
Shodan is a search engine that detects the use of servers (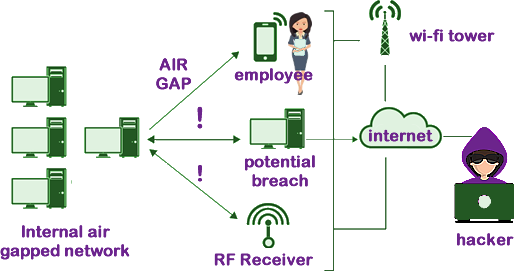
 Complete separation from all external data severely limits what can usefully be accomplished, particularly for tasks that require live or frequent data updates. The protective wall serves as a barrier to updates and data sharing between authorised users.
Complete separation from all external data severely limits what can usefully be accomplished, particularly for tasks that require live or frequent data updates. The protective wall serves as a barrier to updates and data sharing between authorised users.

